
As of 2021, it has been reported that there were over 450 million WordPress websites, or almost 65% of all websites globally. As the world’s most popular web publishing platform, WordPress continues to be the target of hackers.
As such, it may behoove WordPress website administrators to consider implementing some plugins which may help to protect their WordPress websites against hacking.
So, in no particular order, here they are:
Disable REST API By Dave McHale
Did you know that WordPress’ REST API endpoints makes it possible for web developers to remotely access websites by sending and also receiving JSON objects making this functionality extremely useful when building apps within WordPress?
However, the downside of the WordPress REST API is that it could actually more easily expose your WordPress website to brute-force attacks.
What is a Brute-Force Attack?
A brute-force attack is a process by which hackers will try to guess your login credentials (username and password) through an exhaustive (hence the name brute-force) series of guesses with the goal of eventually guessing correctly. Brute-force attacks are among the most common and pervasive methods using to gain access to a WordPress website.
Why could the WordPress REST API be a Security Risk?
By default, WordPress leaves usernames of anyone who has published content on your website accessible to the general public. Allowing open access to your usernames makes it easier for hackers to gain entry to your “back end” because they only need to guess the password (for a given username) rather than trying to guess both the username AND the password.
Realistically, most website owners would be better off with the WordPress REST API disabled.
Once this plugin is installed and activated, the entire REST API will be inaccessible to the public. For most versions of WordPress, this plugin will return an authentication error for all users not permitted to access an endpoint. But, if you must grant access to some endpoints, you can do so via whitelisting individual endpoints within the settings of this plugin.
Limit Login Attempts Reloaded
Limit Login Attempts Reloaded helps to prevent brute-force attacks by limiting the number of login attempts that are permitted through the traditional WP login page in addition to other methods such as XMLRPC, Woocommerce and custom login pages. For example, you can limit the login “allowed retries” to a few as “1” with a max lock out time of up to “9999” minutes. Moreover, you can set the number of lockouts to as few as “1” increase lockout time to hours to “9999” hours
You can also limit the hours until retries are reset to as much as “9999” hours. (see Image below)
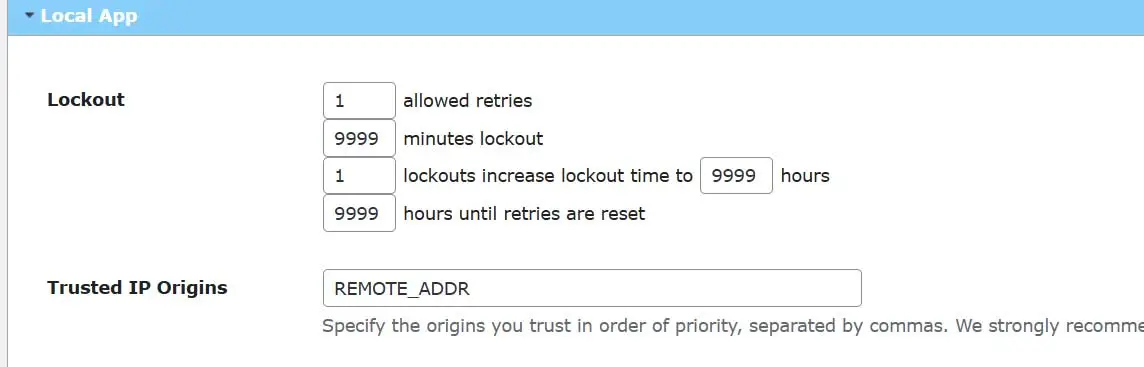
This plugin also give you the ability to whitelist (Safelist) and blacklist (Blocklist) IP addresses and usernames.
Since by default, WordPress permits an unlimited number login attempts, installing Limit Login Attempts Reloaded is recommended to avoid your login credentials from being more easily guessed though a brute-force attack.